Fingerprintg (a.k.a. robust hashing) project covers the follwoing directions:
- passive fingerprinting
- active fingerprinting
- soft fingerprinting
- privacy preserving fingerprinting
See related papers below.
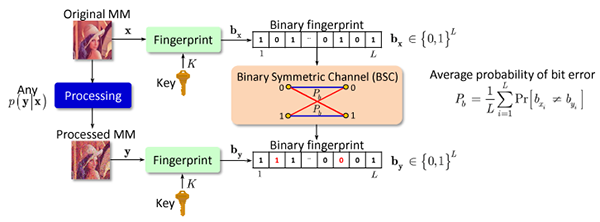
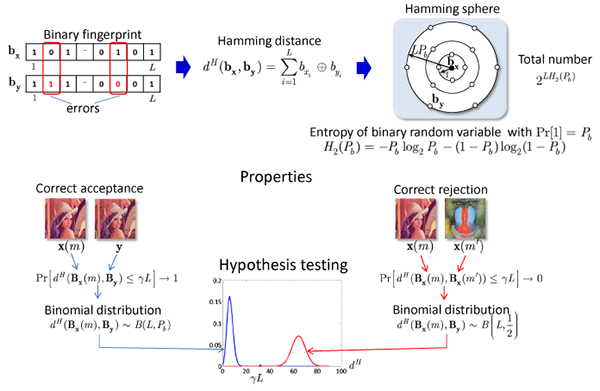
Related publications
Passive fingerprinting for content identification (theory, fast search methods, links to machine learning)
- S. Ferdowsi, S. Voloshynovskiy, and D. Kostadinov, "Content identification: binary content fingerprinting versus binary content encoding," in Proc. Proceedings of SPIE Photonics West, Electronic Imaging, Media Forensics and Security V, San Francisco, USA, 2014. [pdf|bib]
- F. Farhadzadeh and S. Voloshynovskiy, "Active Content Fingerpriting," Information Forensics and Security, IEEE Transactions on, vol. 9, iss. 6, pp. 905-920, 2014. [pdf|bib]
- S. Ferdowsi and S. Voloshynovskiy, "Content identification: machine learning meets coding," in Proc. 35th WIC Symposium on Information Theory in the Benelux, Enschede, the Netherlands, 2014, pp. 113-120. [pdf|bib]
- F. Beekhof, S. Voloshynovskiy, and F. Farhadzadeh, "Content Authentication and Identification under Informed Attacks," inProc. Proceedings of IEEE International Workshop on Information Forensics and Security, Tenerife, Spain, 2012. [pdf|bib]
- T. Holotyak, S. Voloshynovskiy, F. Farhadzadeh, O. Koval, and F. Beekhof, "Fast physical object identification based on unclonable features and soft fingerprinting," in Proc. International Conference on Acoustics, Speech and Signal Processing ICASSP2011, Prague, Czech Republic, 2011. [pdf|bib]
- O. Koval, S. Voloshynovskiy, F. Farhadzadeh, T. Holotyak, and F. Beekhof, "Geometrically robust perceptual fingerprinting: an asymmetric case," in Proc. Proceedings of SPIE Photonics West, Electronic Imaging, Media Forensics and Security XIII, San Francisco, USA, 2011. [pdf|bib]
- F. Farhadzadeh, S. Voloshynovskiy, O. Koval, T. Holotyak, and F. Beekhof, "Statistical analysis of digital image fingerprinting based on random projections," in Proc. Image and Signal Processing and Analysis (ISPA), 2011 7th International Symposium, Dubrovnik, Croatia, 2011. [pdf|bib]
- S. Voloshynovskiy, O. Koval, F. Beekhof, and T. Holotyak, "Theoretic Multiclass Classification Based on Binary Classifiers,"Signal Processing Systems, vol. 65, pp. 413-430, 2011. [pdf|bib]
- F. Farhadzadeh, S. Voloshynovskiy, and O. Koval, "Content Identification Based on digital fingerprint: what can be done if ML decoding fails?," in Proc. IEEE International Workshop on Multimedia Signal Processing, Saint-Malo, France, 2010. [bib]
- F. Farhadzadeh, S. Voloshynovskiy, O. Koval, and F. Beekhof, "Information-theoretic analysis of content based identification for correlated data," in Proc. IEEE Information Theory Workshop (ITW), Paraty, Brazil, 2011, pp. 205-209. [pdf|bib]
- F. Farhadzadeh, S. Voloshynovskiy, O. Koval, T. Holotyak, and F. Beekhof, "Statistical analysis of digital image fingerprinting based on random projections," in Proc. Image and Signal Processing and Analysis (ISPA), 2011 7th International Symposium, Dubrovnik, Croatia, 2011. [pdf|bib]
- T. Holotyak, S. Voloshynovskiy, F. Beekhof, and O. Koval, "Fast identification of highly distorted images," in Proc. Proceedings of SPIE / Media Forensics and Security XII, San Jose, USA, 2010. [pdf|bib]
- F. Farhadzadeh, S. Voloshynovskiy, and O. Koval, "Performance Analysis of Identification System Based on Order Statistics List Decoder," in Proc. IEEE International Symposium on Information Theory, Austin, TX, 2010. [pdf|bib]
- S. Voloshynovskiy, O. Koval, F. Beekhof, F. Farhadzadeh, and T. Holotyak, "Information-Theoretical Analysis of Private Content Identification," in Proc. IEEE Information Theory Workshop, ITW2010, Dublin, Ireland, 2010. [pdf|bib]
- F. Beekhof, S. Voloshynovskiy, O. Koval, and T. Holotyak, "On Accuracy, Privacy and Complexity in the Identification Problem," in Proc. Proceedings of SPIE / Multimedia Content Access: Algorithms and Systems IV, San Jose, USA, 2010. [pdf|bib]
- F. Farhadzadeh, S. Voloshynovskiy, and O. Koval, "Content-Identification: towards Capacity Based on Bounded Distance Decoder," in Proc. Applications of Information Theory, Coding and Security, Yerevan, Armenia, 2010. [pdf|bib]
- S. Voloshynovskiy, O. Koval, F. Beekhof, and T. Pun, "Conception and limits of robust perceptual hashing: toward side information assisted hash functions," in Proc. Proceedings of SPIE Photonics West, Electronic Imaging / Media Forensics and Security XI, San Jose, USA, 2009. [pdf|bib]
- S. Voloshynovskiy, O. Koval, F. Beekhof, and T. Pun, "Robust perceptual hashing as classification problem: decision-theoretic and practical considerations," in Proc. Proceedings of the IEEE 2007 International Workshop on Multimedia Signal Processing, Chania, Crete, Greece, 2007. [pdf|bib]
Active fingerprinting (new alternative to digital watermarking and passive fingerprintig)
- F. Farhadzadeh, F. Willems, and S.Voloshynovskiy, "Information-Theoretical Limits of Active Content Fingerprinting in Content-based Identification Systems," in Proc. Proceedings of IEEE International Workshop on Information Forensics and Security, Rome, Italy, 2015. [pdf|bib]
- F. Farhadzadeh, F. Willems, and S. Voloshynovskiy, "Information theoretical analysis of identification based on active content fingerprinting," in Proc. 35th WIC Symposium on Information Theory in the Benelux, Enschede, the Netherlands, 2014, pp. 134-139. [pdf|bib]
- F. Farhadzadeh and S. Voloshynovskiy, "Active Content Fingerpriting," Information Forensics and Security, IEEE Transactions on, vol. 9, iss. 6, pp. 905-920, 2014. [pdf|bib]
- F. Farhadzadeh, S. Voloshynovskiy, T. Holotyak, and F. Beekhof, "Active content fingerprinting: Shrinkage and lattice based modulations," in Proc. Acoustics, Speech and Signal Processing (ICASSP), 2013 IEEE International Conference on, 2013, pp. 3073-3077. [bib]
- S.Voloshynovskiy, F. Farhadzadeh, O. Koval, and T. Holotyak, "Active content fingerprinting: a marriage of digital watermarking and content fingerprinting," in Proc. Proceedings of IEEE International Workshop on Information Forensics and Security, Tenerife, Spain, 2012. [pdf|bib]
- F. Beekhof, S. Voloshynovskiy, O. Koval, and T. Holotyak, "Fast identification algorithms for forensic applications," in Proc. Proceedings of IEEE International Workshop on Information Forensics and Security, London, UK, 2009. [pdf|bib]
- S. Voloshynovskiy, O. Koval, F. Beekhof, and T. Holotyak, "Multi-class Classifiers based on Binary Classifiers: On Coding Matrix Design, Reliability and Maximum Number of Classes," in Proc. Proceedings of the IEEE International Workshop on MACHINE LEARNING FOR SIGNAL PROCESSING, Grenoble, France, 2009. [pdf|bib]
- S. Voloshynovskiy, O. Koval, F. Beekhof, and T. Pun, "Conception and limits of robust perceptual hashing: toward side information assisted hash functions," in Proc. Proceedings of SPIE Photonics West, Electronic Imaging / Media Forensics and Security XI, San Jose, USA, 2009. [pdf|bib]
- O. Koval, S. Voloshynovskiy, P. Bas, and F. Cayre, "On security threats for robust perceptual hashing," in Proc. Proceedings of SPIE Photonics West, Electronic Imaging / Media Forensics and Security XI, San Jose, USA, 2009. [pdf|bib]
- S. Voloshynovskiy, O. Koval, F. Beekhof, and T. Pun, "Random projections based item authentication," in Proc. Proceedings of SPIE Photonics West, Electronic Imaging / Media Forensics and Security XI, San Jose, USA, 2009. [pdf|bib]
- S. Voloshynovskiy, O. Koval, F. Beekhof, and T. Holotyak, "Binary Robust Hashing based on Probabilistic Bit Reliability," inProc. Proceedings of the Workshop on Statistical Signal Processing, Cardiff, UK, 2009. [pdf|bib]
- O. Koval, S. Voloshynovskiy, F. Beekhof, and T. Pun, "Security Analysis of Robust Perceptual Hashing," in Proc. Steganography, and Watermarking of Multimedia Contents X, (SPIE, Bellingham, WA 2008) 681906, 2008. [ps| link|bib]
Soft fingerprinting (=bits with realability)
- S. Voloshynovskiy, T. Holotyak, and F. Beekhof, "Soft content fingerprinting with bit polarization based on sign-magnitude decomposition," Information Forensics and Security, IEEE Transactions on, vol. PP, iss. 99, pp. 1-1, 2015. [pdf|bib]
- S. Voloshynovskiy, T. Holotyak, O. Koval, F. Beekhof, and F. Farhadzadeh, "Sign-Magnitude Decomposition of Mutual Information with Polarization Effect in Digital Identification," in Proc. IEEE ITW, Paraty, Brazil, 2011. [pdf|bib]
- S. Voloshynovskiy, O. Koval, F. Beekhof, and T. Holotyak, "Binary Robust Hashing based on Probabilistic Bit Reliability," in Proc. Proceedings of the Workshop on Statistical Signal Processing, Cardiff, UK, 2009. [pdf|bib]
Privacy preserving fingerprinting
- S. Voloshynovskiy, M. Diephuis, and T. Holotyak, "Privacy preserving multimedia content identification for cloud based bag-of-feature architectures," in Proc. Workshop on Cloud Based Media in conjunction with the 2015 IEEE International Conference on Multimedia and Expo (ICME 2015), Torino, Italy, 2015. [pdf|bib]
- S. Voloshynovskiy, T. Holotyak, O. Koval, F. Beekhof, and F. Farhadzadeh, "Private content identification based on soft fingerprinting," in Proc. Proceedings of SPIE Photonics West, Electronic Imaging, Media Forensics and Security XIII, San Francisco, USA, 2011. [pdf|bib]
- V. Balakirsky, S. Voloshynovskiy, O. Koval, and T. Holotyak, "Information Theoretic Analysis of Privacy Protection for Noisy Identification Based on Soft Fingerprinting," in Proc. CSIT 2011, Yerevan, Armenia, 2011. [pdf|bib]
- T. Holotyak, S. Voloshynovskiy, O. Koval, and F. Beekhof, "Trading-off privacy-complexity of identification problem," in Proc. Proceedings of SPIE Photonics West, Electronic Imaging, Media Forensics and Security XIII, San Francisco, USA, 2011. [pdf|bib]
- S. Voloshynovskiy, O. Koval, T. Holotyak, F. Beekhof, and F. Farhadzadeh, "Privacy amplification of content identification based on fingerprint bit reliability," in Proc. Proceedings of IEEE International Workshop on Information Forensics and Security, Seattle, The USA, 2010. [pdf|bib]
- S. Voloshynovskiy, F. Beekhof, O. Koval, and T. Holotyak, "On privacy preserving search in large scale distributed systems: a signal processing view on searchable encryption," in Proc. Proceedings of the International Workshop on Signal Processing in the EncryptEd Domain, Lausanne, Switzerland, 2009. [pdf|bib]

